IEEE security conference features six accepted papers from CSE researchers
The projects impact voting systems, physical sensors, integrated circuit fabrication, and multiple microarchitectural side-channel vulnerabilities.

 Enlarge
Enlarge
Researchers at U-M CSE have been accepted to present six papers at the 2020 IEEE Security and Privacy Conference, one of the top conferences in its field. The work by students and faculty has implications for voting systems, physical sensors, integrated circuit fabrication, and multiple microarchitectural side-channel vulnerabilities.
Learn more about the papers:

 Enlarge
Enlarge
Can Voters Detect Malicious Manipulation of Ballot Marking Devices?
This paper earned the conference’s Best Student Paper Award.
Matthew Bernhard (University of Michigan), Allison McDonald (University of Michigan), Henry Meng (University of Michigan), Jensen Hwa (University of Michigan), Nakul Bajaj (The Harker School), Kevin Chang (University of Michigan), J. Alex Halderman (University of Michigan)
In an attempt to adapt the convenience and accessibility of electronic voting machines to more secure and reliable paper ballots, ballot marking devices (BMDs) have voters use a simple touchscreen interface to make their selections. Once they are finished recording votes, the machine prints off their ballot with their choices filled in for them to take to the ballot box. It’s here that voters take responsibility for a crucial verification step – checking that their printed ballot matches their actual choices. This study found that voters missed over 93% of errors on printed ballots that they filled out using electronic BMDs.
 Enlarge
Enlarge
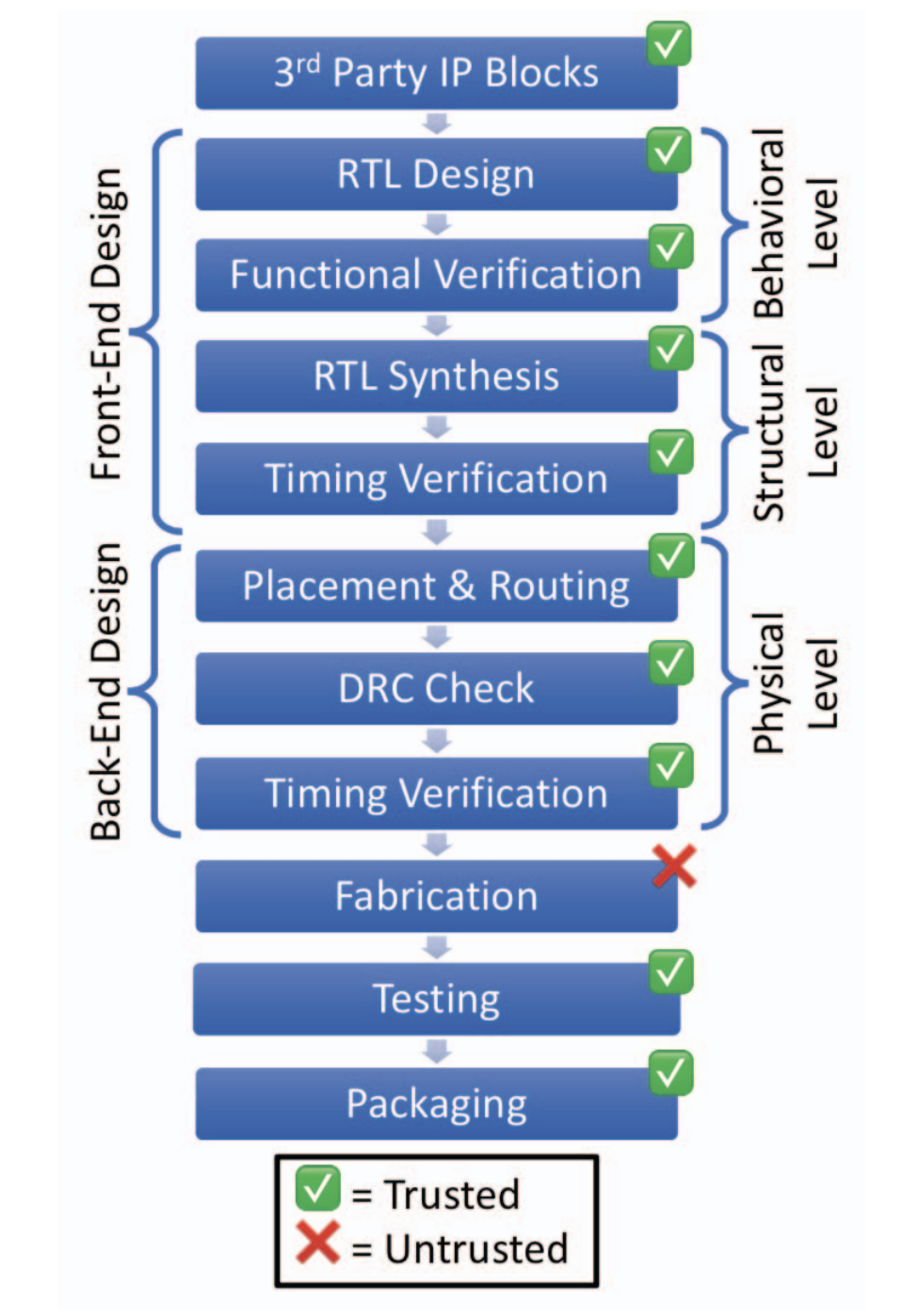
ICAS: An Extensible Framework for Estimating the Susceptibility of IC Layouts to Additive Trojans
Timothy Trippel (University of Michigan), Kang G. Shin (University of Michigan), Kevin B. Bush (MIT Lincoln Laboratory), Matthew Hicks (Virginia Tech)
The transistors used to construct Integrated Circuits (ICs) continue to shrink. While this shrinkage improves performance and density, it also reduces trust: the price to build leading-edge fabrication facilities has skyrocketed, forcing even nation states to outsource the fabrication of high-performance ICs. Outsourcing fabrication presents a security threat because the black-box nature of a fabricated IC makes comprehensive inspection infeasible. IC designers must be able to protect their physical designs before handing them off to an untrusted foundry. Unfortunately, no tool exists to assess the effectiveness of the proposed defenses, thus leaving defensive gaps. This paper presents an extensible IC layout security analysis tool called IC Attack Surface (ICAS) that quantifies defensive coverage. For researchers, ICAS identifies gaps for future defenses to target; for practitioners, ICAS enables the exploration of the impact of design decisions on an IC’s resilience to fabrication-time attack.
 Enlarge
Enlarge
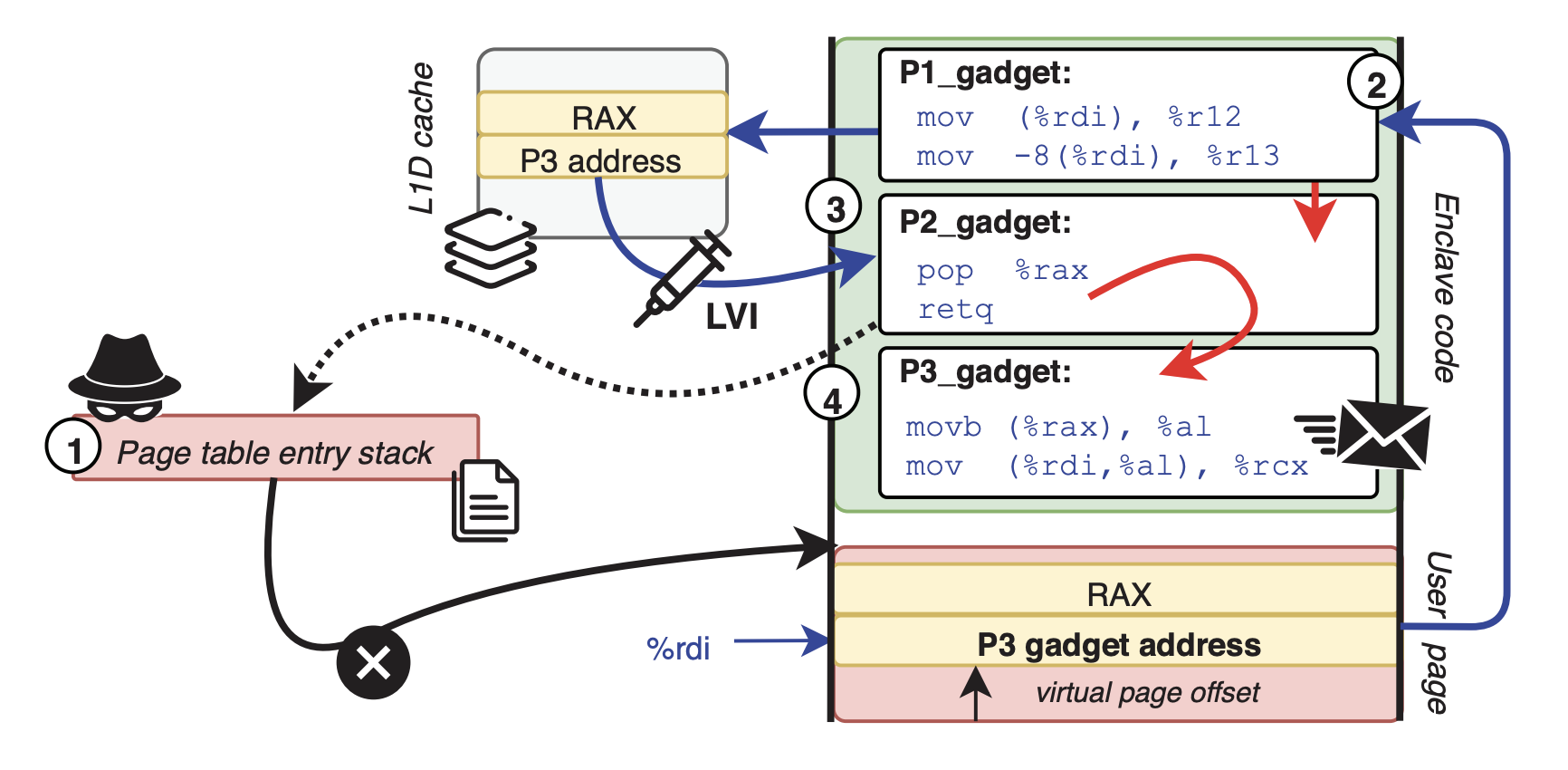
LVI: Hijacking Transient Execution through Microarchitectural Load Value Injection
Jo Van Bulck (imec-DistriNet, KU Leuven), Daniel Moghimi (Worcester Polytechnic Institute), Michael Schwarz (Graz University of Technology), Moritz Lipp (Graz University of Technology), Marina Minkin (University of Michigan), Daniel Genkin (University of Michigan), Yuval Yarom (University of Adelaide and Data61), Berk Sunar (Worcester Polytechnic Institute), Daniel Gruss (Graz University of Technology), Frank Piessens (imec-DistriNet, KU Leuven)
The recent Spectre attack first showed how to inject incorrect branch targets into a victim domain by poisoning microarchitectural branch prediction history. In this paper, the researchers generalize injection-based methodologies to the memory hierarchy by directly injecting incorrect, attacker-controlled values into a victim’s transient execution. They propose LVI as an innovative technique to reversely exploit Meltdown-type microarchitectural data leakage, and practically demonstrate LVI in several proof-of-concept attacks against Intel SGX enclaves.
 Enlarge
Enlarge
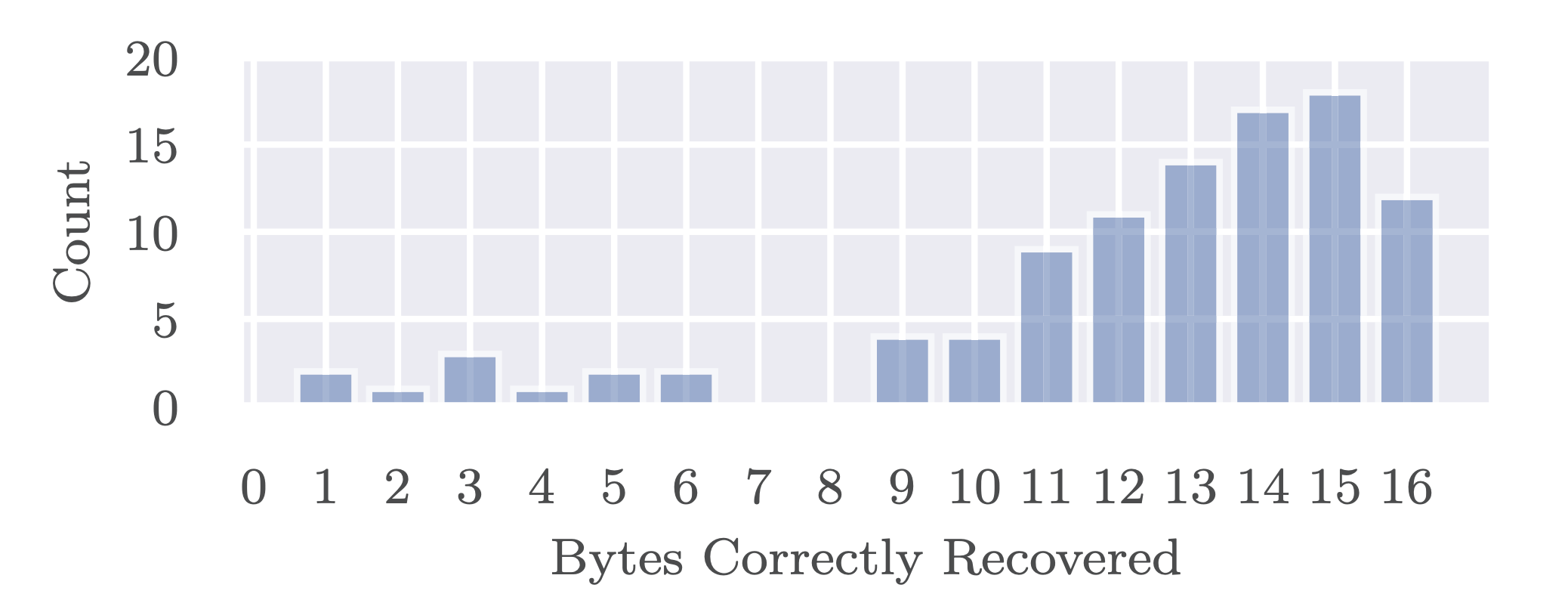
Pseudorandom Black Swans: Cache Attacks on CTR_DRBG
Shaanan Cohney (University of Pennsylvania), Andrew Kwong (University of Michigan), Shahar Paz (Tel Aviv University, Israel), Daniel Genkin (University of Michigan), Nadia Heninger (University of California, San Diego), Eyal Ronen (Tel Aviv University and COSIC (KU Leuven), Israel and Belgium), Yuval Yarom (University of Adelaide and Data61, Australia)
Modern cryptography requires the ability to securely generate pseudorandom numbers. However, despite decades of work on side-channel attacks, there is little discussion of their application to pseudorandom number generators (PRGs). In this work, the researchers set out to address this gap, empirically evaluating the side-channel resistance of common PRG implementations. They find that hard-learned lessons about side-channel leakage from encryption primitives have not been applied to PRGs, at all abstraction levels. They also find that many implementations make parameter choices that enable an attacker to fully exploit side-channels and recover secret keys from TLS connections.
 Enlarge
Enlarge
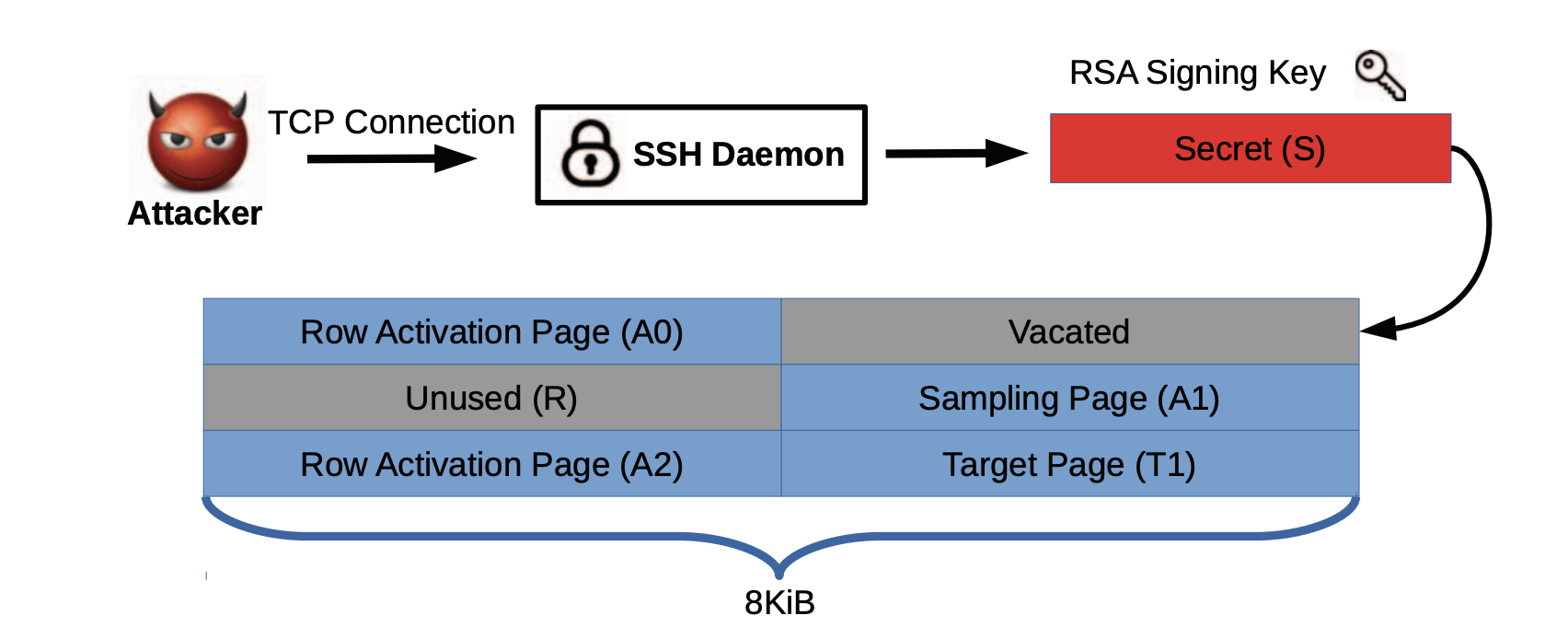
RAMBleed: Reading Bits in Memory without Accessing Them
Andrew Kwong (University of Michigan), Daniel Genkin (University of Michigan), Daniel Gruss (Graz University of Technology), Yuval Yarom (University of Adelaide and Data61)
The Rowhammer bug is a reliability issue in DRAM cells that can enable an unprivileged adversary to flip the values of bits in neighboring rows on the memory module. Previous work has exploited this for various types of fault attacks across security boundaries, where the attacker flips inaccessible bits, often resulting in privilege escalation. It is widely assumed however, that bit flips within the adversary’s own private memory have no security implications, as the attacker can already modify its private memory via regular write operations. The researchers demonstrate that this assumption is incorrect, by employing Rowhammer as a side channel. They show how an unprivileged attacker can exploit the data dependence between Rowhammer induced bit flips and the bits in nearby rows to deduce these bits, including values belonging to other processes and the kernel. This shows that Rowhammer is a threat not only to integrity, but to confidentiality as well.
 Enlarge
Enlarge
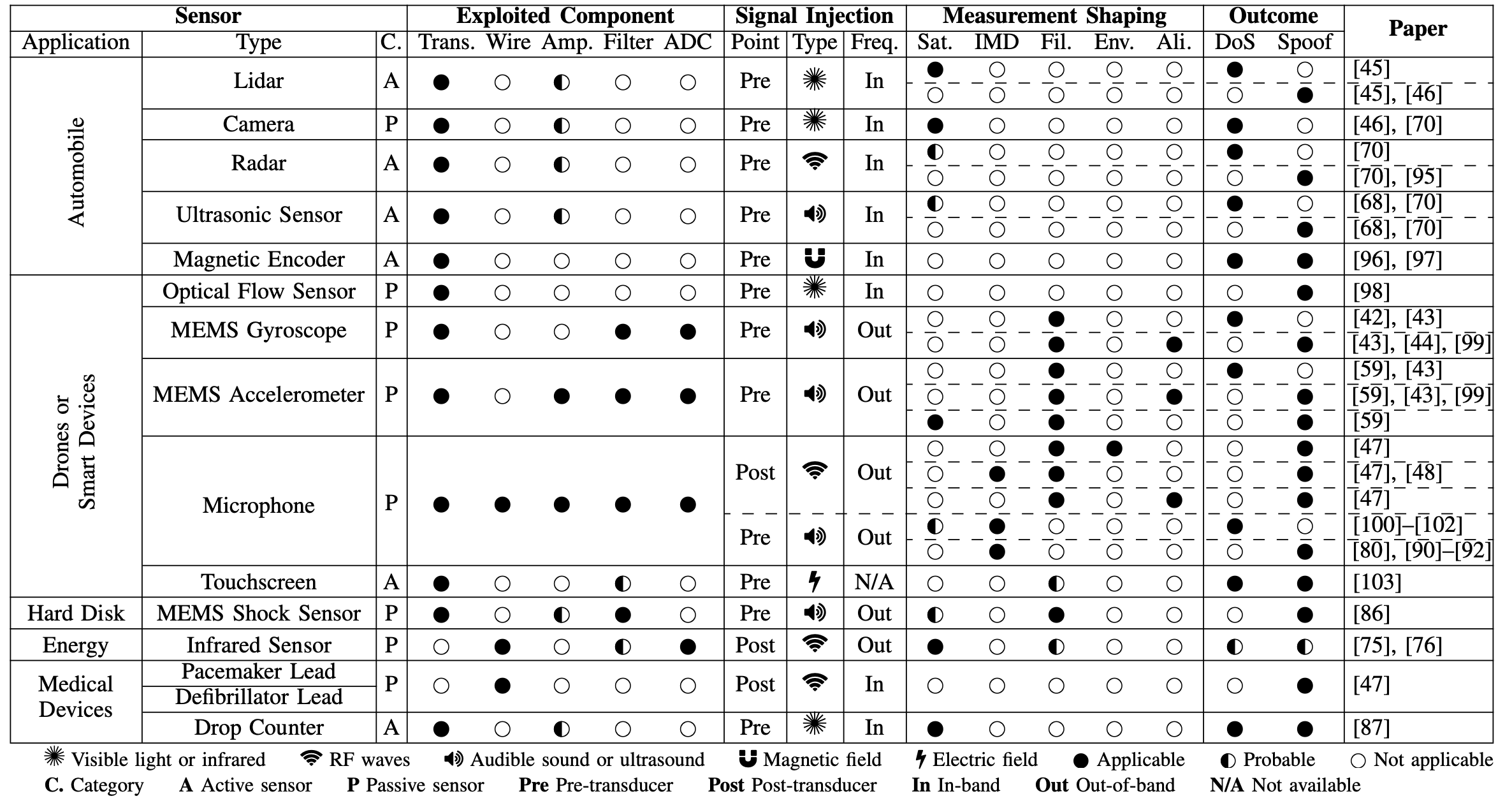
SoK: A Minimalist Approach to Formalizing Analog Sensor Security
Chen Yan (Zhejiang University), Hocheol Shin (KAIST), Connor Bolton (University of Michigan), Wenyuan Xu (Zhejiang University), Yongdae Kim (KAIST), Kevin Fu (University of Michigan)
Over the last six years, several papers demonstrated how intentional analog interference based on acoustics, RF, lasers, and other physical modalities could induce faults, influence, or even control the output of sensors. Damage to the availability and integrity of sensor output carries significant risks to safety-critical systems that make automated decisions based on trusted sensor measurement. Established signal processing models use transfer functions to express reliability and dependability characteristics of sensors, but existing models do not provide a deliberate way to express and capture security properties meaningfully. This work begins to fill this gap by systematizing knowledge of analog attacks against sensor circuitry and defenses. The team proposes a simple sensor security model such that sensor engineers can better express analog security properties of sensor circuitry without needing to learn significantly new notation.
 MENU
MENU 
